| 1. Functions | 2. Reference Model | 3. Input/Output Data |
| 4. Functions of AI Modules | 5. Input/output Data of AI Modules | 6. AIW, AIMs, and JSON Metadata |
1. Functions
The Back End implements the following functionalities:
| Receives | Federated Learn Response | Health Front End’s response to request to provide its trained NN. |
| Audit Request | Health Front End’s to Audit AIH Data. | |
| Licence Confirm Response | Blockchain’s response to Licence Confirmation Request. | |
| DIA Requests | Request to De-Identify and Anonymise AIH Data. | |
| Blockchain Licence Response | Blockchain’s Response to Request to create Smart Contract from Model Licence. | |
| Licence Confirm Response | Response to Request to Blockchain to confirm Licence ID. | |
| AIH Data Process Request | Request to Process AIH Data. | |
| Register Request | User’s Request to Register. | |
| Produces | NN Model | Neural Network sent by Health Front End. |
| Federated Learn Request | Request to Health Front End to provide its trained NNs. | |
| Audit Response | Response to request to Audit AIH Data. | |
| Licence Confirm Request | Request to Blockchain to confirm Licence ID. | |
| DIA Response | Health Back End’s response to request to De-Identify and Anonymise AIH Data. | |
| Blockchain Licence Request | Blockchain’s request to create Smart Contract from Model Licence. | |
| AIH Data Process Response | Health Back End’s response to request to Process AIH Data. | |
| Register Response | Health Back End’s response to User’s Request to Register. |
2. Reference Model
Figure 1 depicts the Reference Architecture of the Health Back End (AIH-HBE) where Back End, End Users, Blockchain, and Third-Party Users perform operation. The term User indicates both End User and Third-Party User.
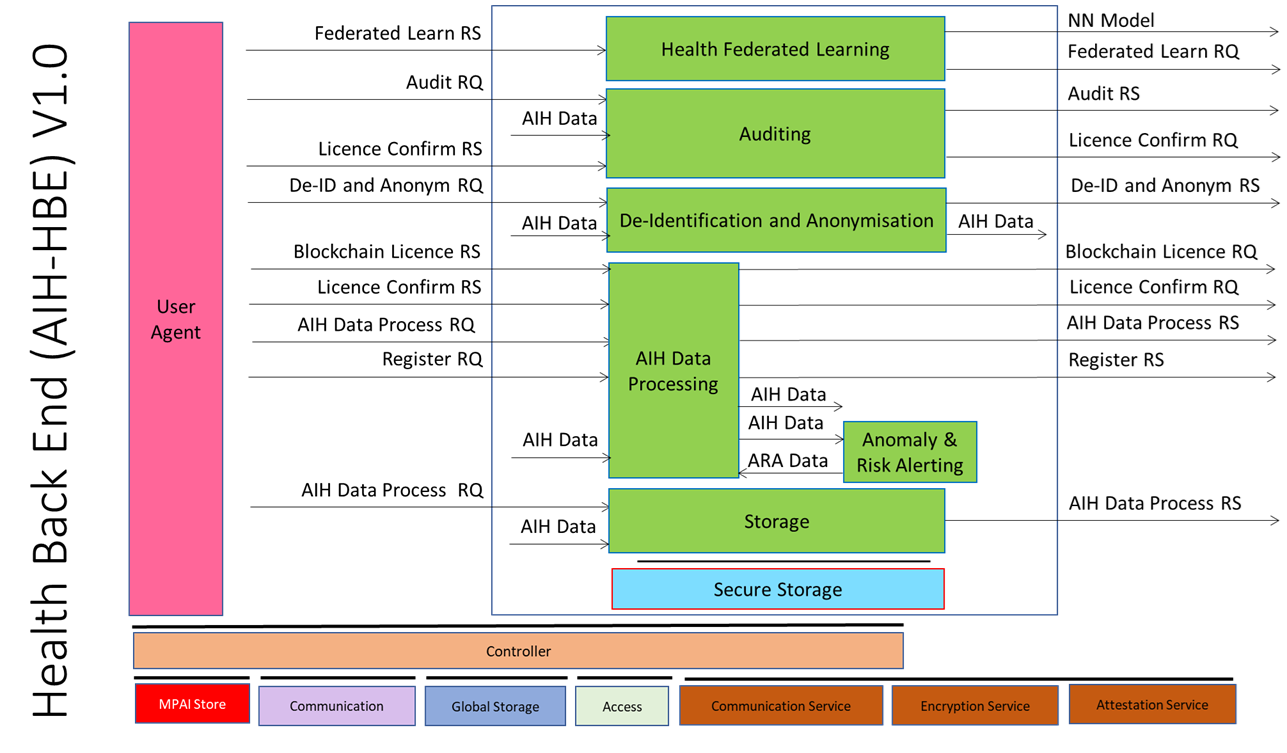
Figure 1 – Reference Model of the Health Back End (AIH-HBE) AIW
- Back End accesses the MPAI Store and downloads the AIMs required for its operation.
- User Registers
- A User wishing to access the Back End, sends a Registration Request containing Personal Profile and list of Service they intend to access.
- Back End provides the Tokens enabling the requesting User to access the corresponding Services.
- Storage of AIH Data
- End User uploads AIH Data.
- HBE Data Processing
- Extracts Model Licence from AIH Data.
- Issues Blockchain Licence Request to Blockchain.
- Blockchain
- Converts Model Licence to a Smart Contract.
- Responds with a Blockchain Licence Request.
- HBE Data Processing
- Attaches Blockchain Licence ID to AIH Data.
- Stores AIH Data in Secure Storage
- De-Identification/Anonymisation (DIA) of AIH Data
- End User sends a DIA Request.
- HBE Data Processing
- Retrieves relevant AIH Data from Secure Storage.
- (Pseudo-)Anonymises AIH Data.
- Stores (Pseudo-)Anonymised AIH Data back to Secure Storage.
- Responds with a DIA Response.
- AIH Data Processing
- User sends AIH Process Request.
- HBE Data Processing sends a Licence Confirm Request to the Blockchain.
- Blockchain responds with a Licence Confirm Response.
- HBE Data Processing
- Performs the requested Processing, if this is included in the Licence.
- Stores the Processed AIH Data as new AIH Data.
- Responds with an AI Data Process Response.
- Audit
- End User sends Audit Request.
- Auditing
- Retrieves relevant Confirmation Responses.
- Responds with Audit Response.
- Federated Learning
- Federated Learning sends Federated Learning Request to all Health Front Ends.
- Health Front Ends provide the NN Models.
- Federated Learning
- Develops and upload the new NN Model to the MPAI Store.
- Sends Federated Learning Response to Health Front Ends.
- Front Ends download the new NN Model from the MPAI Store.
3. Input/Output Data
Table 1 specifies the Input and Output Data.
Table 1 – I/O Data of Health Back End
| Input | Description |
| Federated Learn Request | HBE’s request to End User to produce NN Model. |
| Audit Request | User’s request to Audit Processing of AIH Data. |
| Licence Confirm Response | Blockchain response to request to confirm that a specific Processing on specific AIH Data is allowed by Licence. |
| De-ID and Anonym Request | User’s request to De-Identify and Anonymise AIH Data. |
| Blockchain Licence Response | Blockchain’s response to request to provide ID of Licence based on Model Licence |
| Licence Confirm Response | Blockchain response to a request that a specific Processing on specific AIH Data is allowed by Licence |
| AIH Data Process Request | User’s request to Process AIH Data. |
| Register Request | User’s request to Register |
| Output | Description |
| ML Model Object | NN Model sent to MPAI Store after completing Federated Learning process. |
| Federated Learn Response | Health Front End’s response to Federated Learning Request. |
| Audit Response | User’s request to Audit AIH Data for Processing. |
| Licence Confirm Request | Request to Blockchain that a specific Processing on specific AIH Data is allowed by Licence |
| De-ID and Anonym Response | HBE Data Processing’s response to DIA Request. |
| Blockchain Licence Request | Request to Blockchain for Licence. |
| Licence Confirm Response | Blockchain response to a request that a specific Processing on specific AIH Data is allowed by Licence |
| AIH Data Process Response | HBE Data Processing’s response to User’s AIH Data Processing Request. |
| Register Response | Response to Register Request. |
4. Functions of AI Modules
Table 2 specifies the Function of the AI Modules.
Table 2 – Functions of Health Back End AI Modules
| AI Module | Description |
| Health Federated Learning | Performs Federated Learning of Front Ends’ NN Model. |
| Auditing | Enables End User to monitor the use of their AIH Data. |
| De-Identification and Anonymisation | De-identifies/(pseudo-)anonymise AIH Data. |
| AIH Data Processing | Processes AIH Data. |
| Anomaly and Risk Alerting | |
| Storage | Stores AIH Data (a type of AIH Processing) |
5. Input/output Data of AI Modules
Table 3 specifies the Function of the AI Modules.
Table 3 – Functions of Health Back End AI Modules
| AI Module | Receives | Produces |
| Health Federated Learning | Federated Learn Response | NN Model |
| Federated Learn Request | ||
| Auditing | Audit Request | Audit Response |
| Licence Confirm Response | Licence Confirm Request | |
| De-Identification and Anonymisation | De-ID and Anonym Request | De-ID and Anonym Response |
| AIH Data | AIH Data | |
| AIH Data Processing | Blockchain License Response | Blockchain License Request |
| Licence Confirm Response | Licence Confirm Request | |
| AIH Data Process Request | AIH Data Process Response | |
| AIH Data | AIH Data | |
| ARA Data | ||
| Storage | AIH Data Process Request | AIH Data Process Response |
| AIH Data | ||
| Register Request | Register Response |
6. AIW, AIMs, and JSON Metadata
Table 4 provides the links to the AIW and AIM specifications and to the JSON syntaxes. AIMs/1 indicates that the column contains Composite AIMs and AIMs indicates that the column contains their Basic AIMs.
Table 4 – AIW, AIMs, and JSON Metadata
| AIW | AIMs | Name | JSON |
| AIH-HBE | Health Back End | X | |
| AIH-HFL | Health Federated Learning | X | |
| AIH-ADT | Auditing | X | |
| AIH-DIA | De-Identification and Anonymisation | X | |
| AIH-HDP | AIH Data Processing | X | |
| AIH-ARA | Anomaly and Risk Alerting | X | |
| AIH-STR | Storage | X |

